Successful companies must scale up their IT infrastructure to accommodate higher data volumes and growing workflow demands. However, introducing new elements to a network can increase the number of attack surfaces and vulnerabilities that hackers may exploit.
So, how can you harden your company’s security posture, even at scale? How can you mitigate cyber risks and protect sensitive data from falling into the wrong hands?
The answer is with effective attack surface management.
This article will explain attack surfaces and why managing them is more important than ever. We’ll also look at how solutions from Spinnaker Support can help improve your security posture and harden your enterprise system.
What is an attack surface?
An attack surface is the collected total of all possible attack vectors that hackers could potentially exploit to access a network. Vulnerabilities can be present across multiple levels of your IT stack, including applications, system software, hardware devices, and user accounts. A breach of such vulnerabilities can lead to data leaks, financial losses, and reputational damage.
While the recent shift to cloud computing has allowed companies to scale and meet higher workloads, it’s also led to more potential attack surfaces that threat actors can exploit.
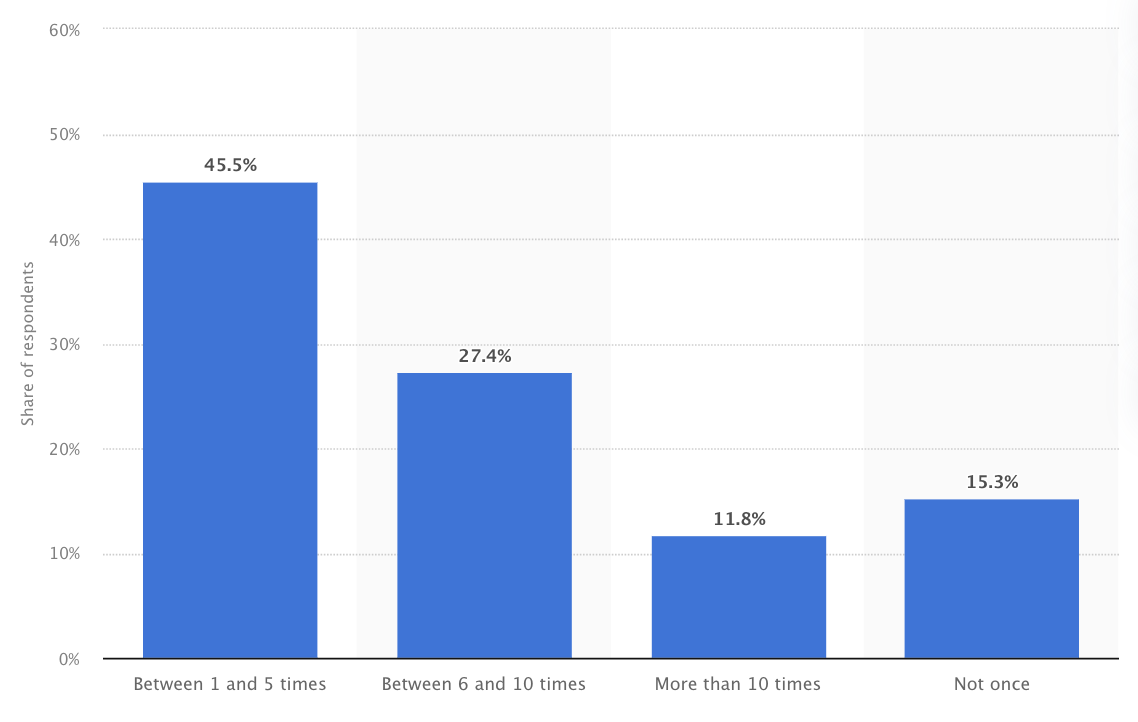
In 2022, 45% of IT security professionals reported one to five successful cyberattacks against their company’s network. Nearly 12% say their organization has experienced over ten successful cyber attacks.
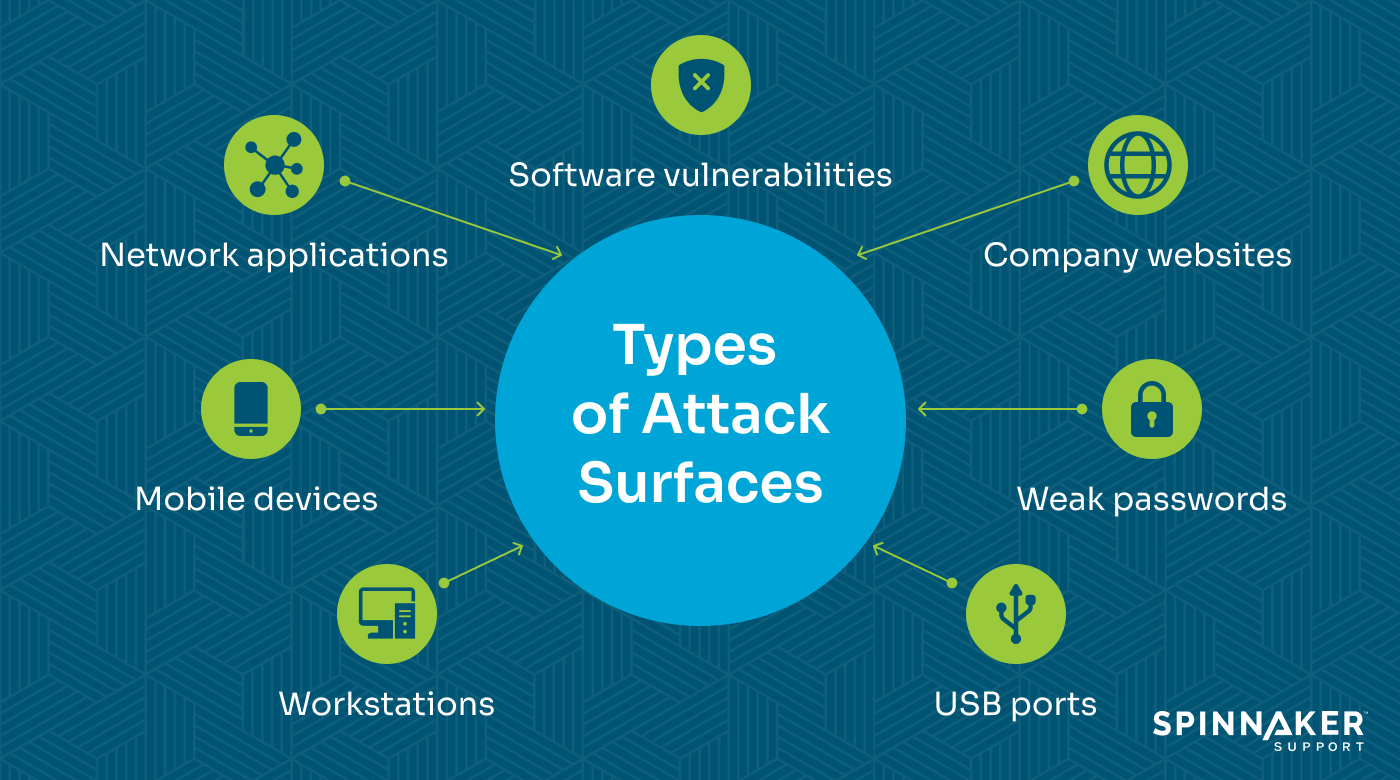
Three types of attack surfaces include:
- Physical attack surface: Encompasses vulnerabilities in physical assets and endpoint devices like desktops, mobile devices, USB ports, and servers. If a mobile device is left behind, an attacker can attempt to extract sensitive data.
- Digital attack surface: Covers all digital elements attackers can exploit to access an organization’s network. Examples include software vulnerabilities, misconfigured network ports, and outdated databases.
- Social engineering attack surface: Uses manipulation techniques to get people, typically employees, to share information or download malware. Common examples include phishing emails that include links to fake login pages.
The Common Vulnerabilities and Exposure (CVE) system is used to track known software vulnerabilities that could create weaknesses in your attack surface. For example, CVE-2022–21445 allowed unauthenticated attackers to gain unauthorized access to Oracle JDeveloper. This vulnerability could be a potential attack vector against any users running JDeveloper in their tech stack.
The next section will look at how companies can manage attack surfaces.
What is attack surface management, and why is it important?
Attack surface management involves identifying and reducing the number of security vulnerabilities in an organization’s network. By taking measures to shrink your attack surface, you can harden your security posture and reduce cyber risk.
These measures can include:
- Limiting user access rights
- Patching and updating software
- Performing risk assessments
- Monitoring IT infrastructure
- Implementing security training
Here’s why attack surface management is essential for any organization.
Mitigate security vulnerabilities
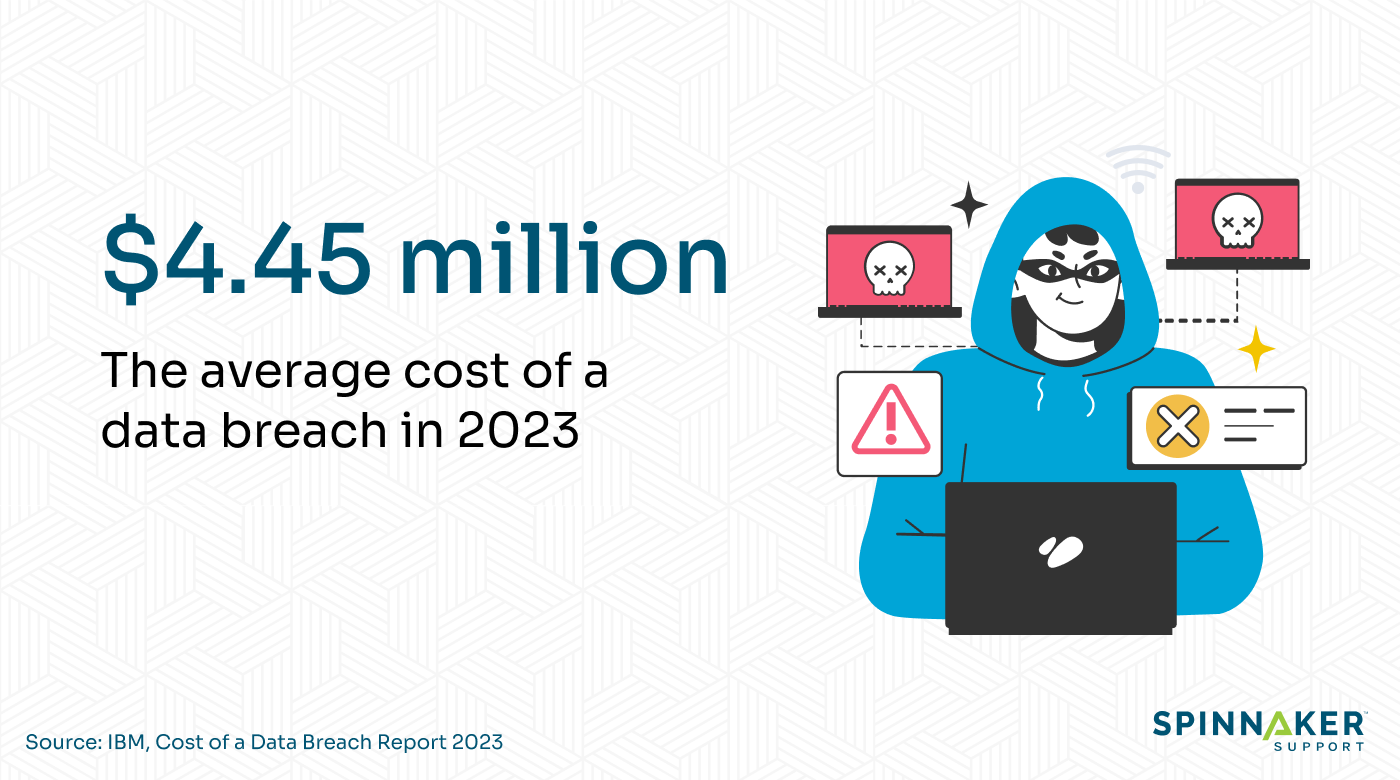
The average cost of a data breach is $4.45 million.
If you’re running outdated software, you run the risk of an attacker exploiting a vulnerability. Part of attack surface management entails conducting vulnerability assessments and identifying potential weaknesses.
For example, our experts assessed a vulnerability in a civic organization’s database and Oracle Enterprise Business Suite (EBS). The most concerning vulnerability we found was an incorrect external node configuration that an attacker could exploit to export database information. This allowed us to provide a list of remedial actions to address the issue.
Click here to read the security success case study.
Avoid costly business disruptions
In March 2018, hackers compromised and held the city of Atlanta’s computer networks at ransom, demanding $51,000 in digital currency to restore access.
The city refused.
As a result, employees had to revert to pen and paper to render certain services. The systems were down for nearly a week, but one report estimates the attack cost the city $17 million — a figure multitudes higher than the original ransom.
The attack illustrates the financial impact of a successful cyberattack. Companies can minimize the financial costs associated with such occurrences by proactively managing attack surfaces. They can also maintain business continuity by developing and testing a continuity plan.
Meet regulatory and compliance requirements
Many companies are subject to industry-specific cybersecurity requirements, such as:
- Payment Card Industry Data Security Standard (PCI DSS): Applies to companies that store and process cardholder data.
- Health Insurance Portability and Accountability Act of 1996 (HIPAA): Applies to healthcare providers that handle sensitive patient information.
- National Institute of Standards and Technology (NIST): Applies to federal government agencies and contractors handling government data.

Non-compliance with cybersecurity requirements can result in stiff penalties.
Anthem was ordered to pay $16 million to the Department of Health and Services after a 2015 data breach exposed the personal health information of nearly 79 million people.
An investigation revealed that Anthem:
- Failed to conduct an enterprise-wide analysis
- Had insufficient system monitoring procedures
- Failed to identify and respond to known security incidents
- Failed to implement minimum access controls
Penalties are just the tip of the iceberg for non-compliance. Breaches like the one described above can cause reputational damage and even result in legal action.
Now, let’s look at an effective attack surface management plan.
The 5 steps of attack surface management
The best way to minimize attacks against your infrastructure is to take a proactive approach. An attack surface management plan consists of the following steps:
1. Asset discovery
The first step in attack surface management is asset discovery. This involves identifying and cataloging assets that can connect to a company’s network.
These include:
- Hardware devices
- Software applications
- Third-party integrations
- Cloud-based systems
- Vendor assets
The goal is to develop a complete “map” of your IT assets, so you can clearly identify any and all potential entry points.
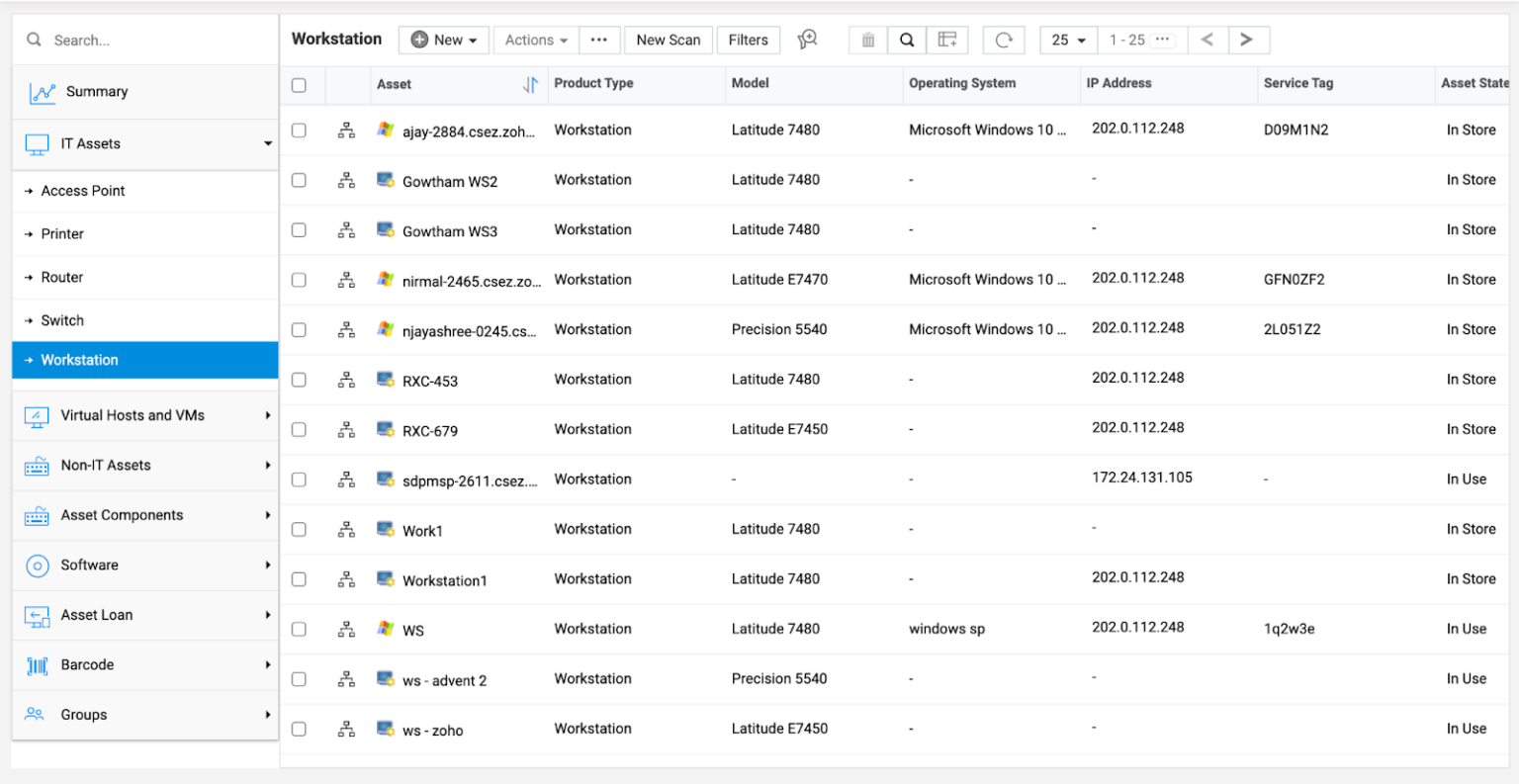
Start by identifying all assets within your infrastructure. Even small organizations can have a large attack surface with dozens or hundreds of hardware, software, and cloud assets. Consider using automated tools and network scanners to create an asset inventory. Record details about each asset, including name, description, version, and other relevant information.
Tools like ManageEngine can be used to scan your network and create a list of all connected assets including details like product type, operating system, and IP address.
Designate a person or team to manage your asset inventory. They should conduct regular reviews to ensure its accuracy and completeness.
2. Vulnerability assessment
The next step involves assessing each asset and identifying potential vulnerabilities. The goal is to uncover any existing flaws or misconfigurations that attackers could exploit.
Companies can use a variety of complementary methods to conduct vulnerability assessments. These include:
- Automated vulnerability scanning: A type of scanning in which automated tools scan systems, networks, and applications. They compare current versions and configurations against a database of known vulnerabilities and report potential weaknesses.
- Penetration testing: A simulated cyberattack where a security professional will attempt to access a computer network. One example is using social engineering attacks like phishing to test the “human” aspect of security.
- Web application testing: Focuses on testing the security of web-based applications. It typically uses Dynamic Application Security Testing (DAST) tools to identify common vulnerabilities, like SQL injections and cross-site scripting (XSS).
Other methods that security experts employ to conduct vulnerability assessments may include conducting manual code reviews and assessing the configuration settings of all systems.
3. Risk prioritization
Risk prioritization helps organizations determine which issues to focus on first. Prioritization criteria may include:
- Potential business impact
- Likelihood of exploitation
- Attack vector accessibility
- Remediation difficulty
- Impact on compliance
One way to prioritize threats like software vulnerabilities is with the Common Vulnerability Scoring System (CVSS) — an industry standard for assessing vulnerabilities based on CVEs.
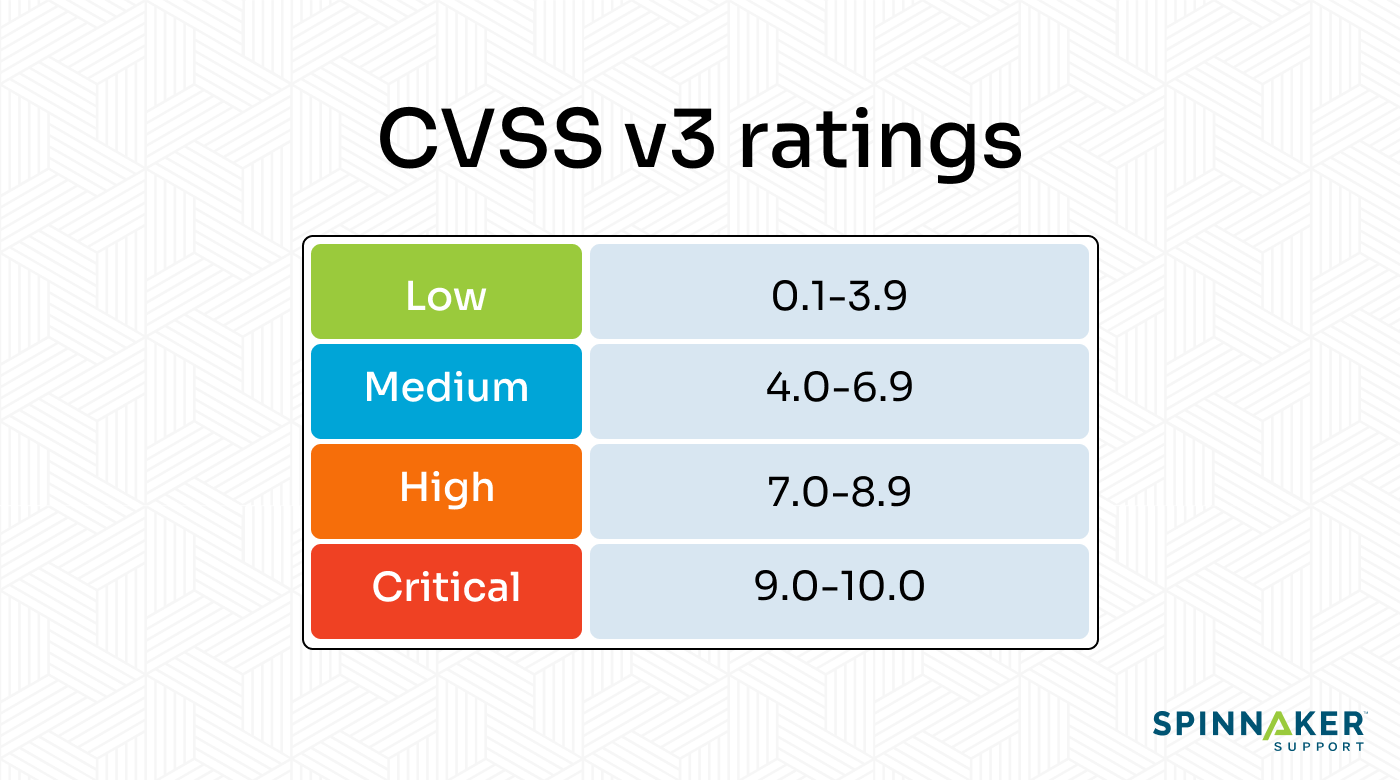
CVSS rates vulnerabilities from low to critical. If a scanning tool detects critical issues, it makes sense to prioritize them.
Start by identifying and categorizing security risks. Then, assess each risk’s likelihood and business impact and use a numerical scale to assign scores. To help with this step, consider working with a third-party support provider like Spinnaker Support to evaluate your enterprise system.
4. Threat remediation
Once you identify and prioritize risks, the next step is remediation. The goal here is to reduce or eliminate vulnerabilities within the attack surface.
Depending on the nature of the vulnerability, remediation efforts may include:
- Updating unpatched software and operating to the latest version
- Implementing strong access controls, such as two-factor authentication (2FA)
- Encrypting network communications to protect sensitive information
- Educating employees about cybersecurity best practices
- Deactivating endpoint devices that are no longer in use
These are just a few of the remediation actions that organizations can take. It’s important to assess and update remediation procedures to address emerging threats continually.
Threat remediation case study
Our experts conducted a vulnerability assessment for a North American paper manufacturer running Oracle Database 11g. We identified a critical vulnerability that could allow attackers to exploit the Integrated Lights Out Manager (ILOM) component and access their systems. It was rated at a risk level of 10.
However, there was a problem; the client couldn’t access patches from Oracle. And if they did, they would’ve had to install a massive patch with 153 fixes for products that weren’t relevant to them. This would mean wasting valuable time on testing and validation.
Fortunately, they didn’t have to.
Our experts implemented and tested a solution that restricts ILOM access via a firewall by only allowing approved IP addresses on an as-needed basis — all within three days.
Click here to learn how Spinnaker Shield keeps your enterprise system secure.
5. Continuous monitoring
Continuous monitoring is an essential aspect of attack surface management. It involves ongoing observation of networks to proactively identify vulnerabilities, security risks, and drifts in compliance posture.
The traditional approach has been to monitor your infrastructure manually. However, this is extremely time-consuming and resource-intensive. It also ties up your IT teams doing work that is, frankly, monotonous.
Another option is to work with a third-party support provider like Spinnaker Support. We rely on automated tools to actively monitor your entire IT infrastructure, encompassing web servers, databases, and applications. This allows us to identify and respond to potential breaches in real time, before they escalate.
We compare our clients’ systems to Center for Internet Security (CIS) recommendations to ensure they meet stringent industry benchmarks for cybersecurity and compliance, including regulatory standards such as HIPAA, PCI, and FISMA.
Attack surface management best practices
Companies today are more vulnerable to cyber attacks than ever. These attack surface management best practices can help.
Stay informed about emerging cybersecurity threats
Attackers continuously evolve their tactics, and new vulnerabilities are discovered daily.
Stay updated with the latest cybersecurity threats so you can equip yourself with the knowledge to protect your systems. Monitoring industry publications and subscribing to security blogs are great ways to stay informed.
Educate employees on cybersecurity best practices
Social engineering is one of the most effective tactics for hackers. 74% of all data breaches involve the human element. Provide regular training to educate your employees about cybersecurity best practices, like recognizing phishing attempts and using strong passwords.
Engage third-party support providers
Attack surface management requires dedicated time and resources. Not only do you need the right tools to monitor your attack surface, but you also need a team with the right training to identify and mitigate risks.
Outsourcing attack surface management to a third-party support provider like Spinnaker Support offers a more cost-effective alternative, allowing you to avoid the ongoing expense of maintaining an in-house team.
Regarding keeping your enterprise system secure, we offer a robust Seven-Point Security Solution that delivers best-in-class security across your infrastructure.
Here’s how our security solution compares to software publisher patching:
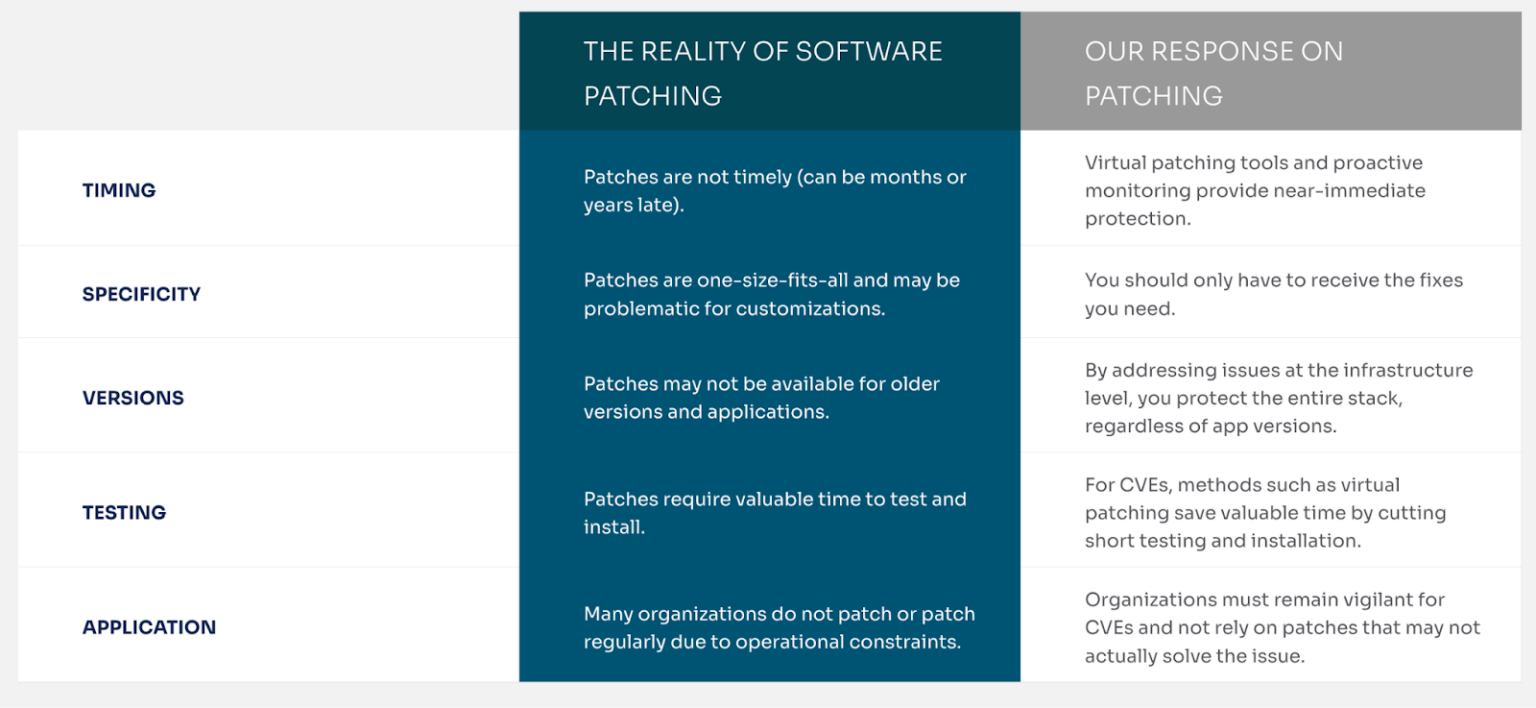
Our security solutions are uniquely designed for your infrastructure. Our team continuously investigates security issues and delivers timely fixes to protect your environment.
Conclusion
The growing shift to cloud infrastructure and transition to remote work has greatly contributed to larger attack surfaces for many organizations. One unsecured device is all it takes for a threat actor to compromise a network.
Effective attack surface management is critical for companies to mitigate security vulnerabilities. It can ensure business continuity and compliance with cybersecurity standards.
Whether your company uses Oracle, SAP, JD Edwards, or other enterprise software solutions, our experts can help enhance your security posture.
Contact us today to speak with a security expert.


